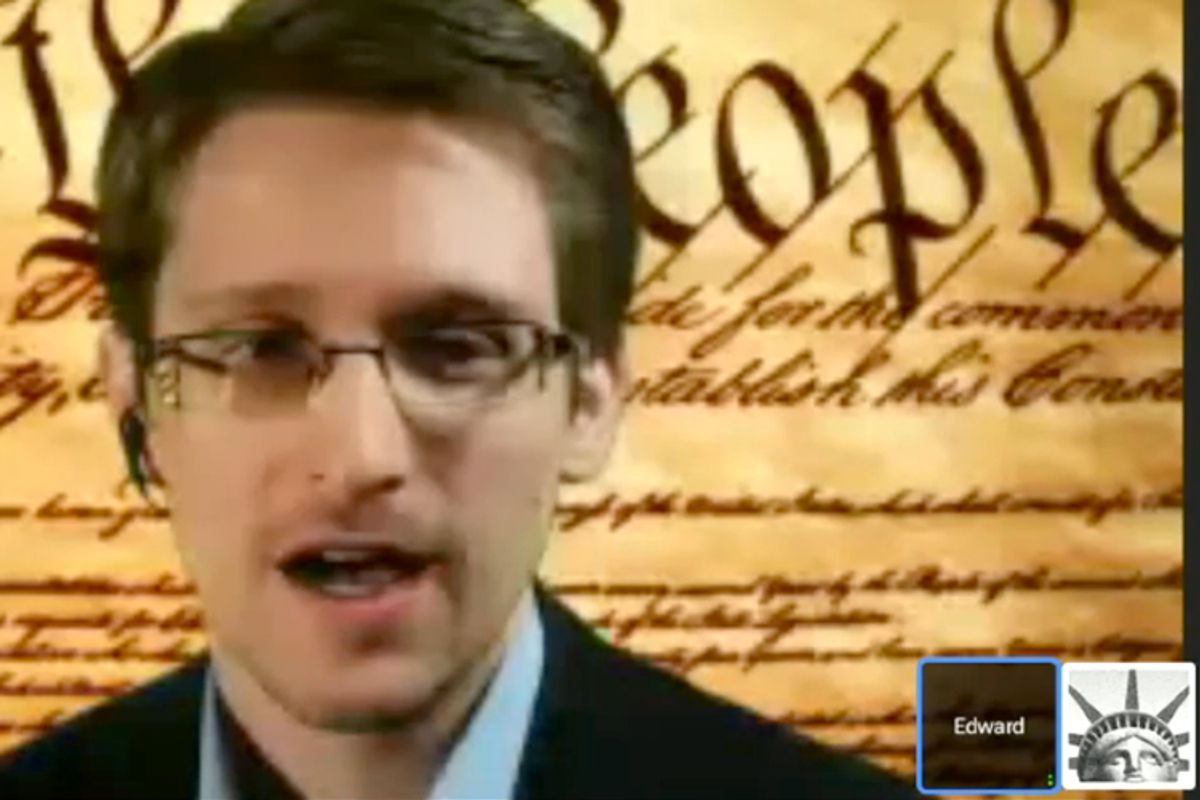
Last week NSA whistle-blower Edward Snowden spoke to a crowd at SXSW Interactive, his first digital American appearance since the former NSA contractor leaked documents detailing the agency's mass surveillance. His message to both future tech start-ups and big tech companies alike was encrypt, encrypt, encrypt. Full disk encryption, end-to-end communication encryption, network encryption -- he stressed, "Encryption does work." He argued that encryption makes mass surveillance too expensive a practice; the NSA would have to narrow its targets rather than sweeping up large swaths of Americans' data. The NSA has received data, via FISA court orders, from many large tech companies such as Google, Facebook, Microsoft and Yahoo.
Today, however, Twitter announced it was doing the exact opposite. The Verge learned from sources that it is dropping plans to encrypt direct messages between users. (The original plan to encrypt was reported by the New York Times in November of 2013.) Twitter has yet to give details as to why the plans were dropped.
Twitter is a mostly public platform known for its ability to spread information and even collectively rally activists, and spur outrage. It does have a private message system, direct messages, or DMs. If your Twitter account has been hacked, you probably mass spammed followers via direct messaging.
Twitter is also known for resisting government requests for data. According to The Verge:
"Twitter has also repeatedly challenged government subpoenas and gag orders, empowered by principles espoused by its founders and the leadership of its strong-willed advisor and former head lawyer, Alex Macgillivray, who one source says "doesn’t give a shit" about the government’s demands or intimidation tactics."
Despite this setback in direct message encryption, Twitter ramped up its security in other ways. Its emails to users are encrypted and according to Twitter's blog, "If an adversary is currently recording all Twitter users’ encrypted traffic, and they later crack or steal Twitter’s private keys, they should not be able to use those keys to decrypt the recorded traffic," as part of their forward secrecy program. The Verge also points out that they have a perfect score from the Electronic Frontier Foundation in both the 2013 "Who Has Your Back?" and "Encrypt the Web" reports.
h/t The Verge


Shares