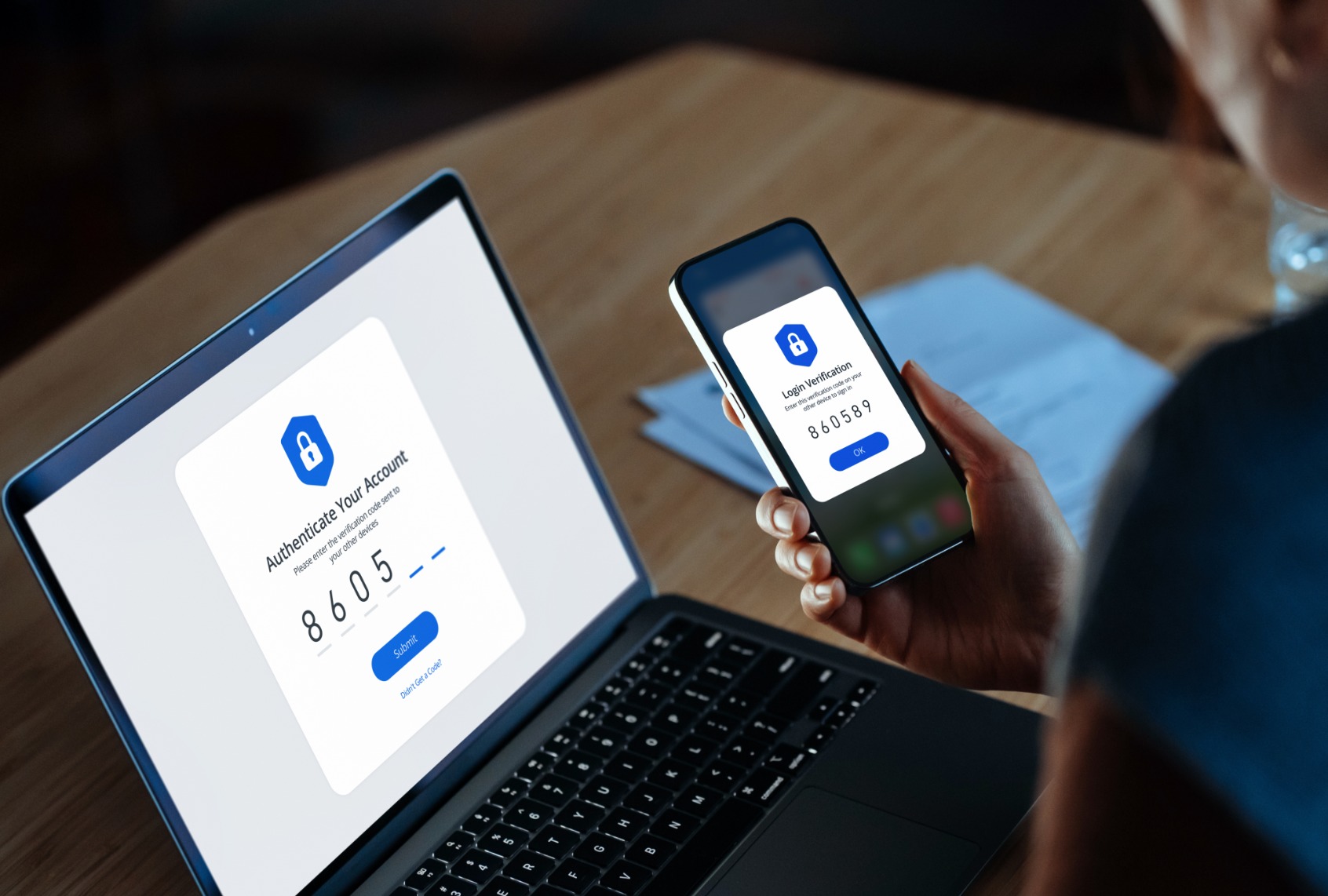
Two-factor authentication (2FA) has emerged as a critical tool to prevent cybercrime. This functionality provides an additional layer of security beyond traditional password-based authentication.
By requiring users to provide additional verification, such as a code sent to their mobile device, 2FA has made it more challenging for cybercriminals to gain unauthorized access to user accounts.
However, as hackers continue to refine their tactics, experts say users need more than 2FA to guarantee security.
The Potential Pitfalls of 2FA
While 2FA enhances security, it can also foster a false sense of confidence. 2FA seems foolproof, leading many people to pay less attention to other security practices, like using strong, unique passwords for each account.
The effectiveness of 2FA varies considerably depending on the specific implementation method employed. SMS-based 2FA (i.e., a code sent by text message) is particularly vulnerable to a range of attacks, including SIM swapping, where cybercriminals trick mobile carriers into transferring a victim's phone number to a SIM card under their control, allowing them to intercept 2FA codes and gain access to the associated accounts.
"In the world of cybersecurity, adaptability is key," said Alissa Knight, Managing Partner at Knight Group. "The future of authentication lies in methods resilient to human error and technological compromise, such as hardware-based keys or biometric verification. It's not about making it impossible to hack—it's about making it not worth the effort. Cybersecurity controls should always be implemented in layers like an onion," she explained.
"An emerging layer that should be included as a Best Practice is the ability to capture 'proof of life' behind the device," said authID CEO Rhon Daguro. "The current multi-layer approach assumes or guesses who the person behind the device is, so with liveness of biometrics, we no longer have to guess, we can capture 'proof of life' of the real person behind the device. Adding a biometrics layer will complete your security best practices in the modern era."
The lack of encryption in SMS messages also renders them susceptible to interception by hackers, further undermining the security of this 2FA method.
The Evolving Threat Landscape: How Hackers Circumvent 2FA
As 2FA has become more widely adopted, hackers have developed increasingly sophisticated techniques to bypass security measures.
One particularly insidious tactic is the man-in-the-middle (MitM) attack, in which a hacker intercepts the communication between a user and a service provider and captures the 2FA code. This approach allows the attacker to log in as the user without their knowledge, often before the victim realizes their account has been compromised.
Phishing attacks are also effective in circumventing 2FA. The user may receive a message containing a link to a fraudulent login page that closely mimics a legitimate site. When the user enters their credentials and 2FA code, the fake site relays this information to the actual site, enabling the hacker to access the user's account. Advanced phishing kits can even intercept 2FA codes in real time, allowing attackers to log in before the user becomes aware of the breach.
We need your help to stay independent
Complacency and Single Points of Failure: The Risks of Over-Reliance on 2FA
One of the dangers associated with 2FA is the potential for user complacency. When individuals feel overly secure, they may become less vigilant about other essential security measures, such as being cautious of phishing attempts or regularly updating their passwords. This false sense of security can be problematic in the face of increasingly sophisticated phishing attacks.
Using the same device for password entry and 2FA reception creates a single point of failure if the device is compromised by malware. If an attacker gains control of a user's device, they may be able to access both the password and the 2FA code, effectively rendering the additional security layer moot.
Best Practices for Secure Authentication in the Modern Era
To mitigate the risks associated with 2FA and ensure a robust security posture, individuals and organizations need to adopt a multi-layered approach to authentication and access control. Some critical best practices include:
1. Implementing strong, unique passwords for each account and utilizing password management tools for secure password storage and generation.
2. Favoring more secure 2FA methods, such as authenticator apps (such as Duo Security and Google Authenticator) or hardware security keys, (such as Yubico) over SMS-based 2FA.
3. Remaining vigilant against phishing attempts by scrutinizing the source and legitimacy of all messages before clicking on links or entering sensitive information.
4. Periodically review and update security settings, including 2FA methods and trusted contacts, to ensure that accounts remain secure even if devices are lost or compromised.
5. Advanced log-in systems, such as WebAuthn and U2F, leverage cryptographic keys to verify user identity for high-value accounts and sensitive data.
Want a daily wrap-up of all the news and commentary Salon has to offer? Subscribe to our morning newsletter, Crash Course.
Empowering Consumers Through Cybersecurity Education
As digital threats grow, consumers must understand their role and stay up to date on the latest security risks and best practices to protect data and accounts.
Consumers can protect themselves against digital threats by learning and adopting a proactive approach to cybersecurity. Security websites such as Krebs on Security and The Hacker News are two reputable sources. As people become better at spotting and reducing risks, they improve their own security and help make the online world safer for everyone.
"Users must keep up in this cat-and-mouse game," said Joe Gaczewski, CISO at Tokio Marine Highland. "The latest tool offered by some browsers and devices is the passkey… 2FA is better than a password only, but we must be mindful of fatigue and mindlessly clicking 'approve.'"
Embracing a Multi-Layered Approach to Authentication Security
As the cyber threat landscape continues to evolve at an unprecedented pace, 2FA, while useful in the fight against cybercrime, is not a silver bullet. To safeguard their data and assets, individuals and organizations must adopt a multi-layered approach to authentication security, combining 2FA with other essential best practices, such as strong password management, regular device and software updates, and ongoing user education.
Read more
about money
- Curious about adding solar power to your home? Watch out for scams
- Prenup panic: J.Lo and Ben Affleck's split highlights the cost of skipping legal prep
- "Shocking": Experts warn "irresponsible" Project 2025 Medicare proposal would harm seniors
- Experts: Housing crisis is increasing generational wealth gap — Harris' plan could have a big impact